
In today’s digital age, securing personal data has become paramount. As users, we need to take into account the platforms and tools we use regularly. /e/OS is the open-source mobile operating system focused on privacy, that has emerged as a noteworthy solution to this challenge. This post is a comprehensive guide on how to utilize encrypted emails in /e/OS to bolster your digital privacy.
Understanding /e/OS
/e/OS is a privacy-focused fork of Android, designed to minimize data leakage and remove reliance on most Google services. It offers an array of apps and a cloud storage service, all engineered to uphold user privacy and safeguard data.
The Need for Encrypted Emails
Email, despite the popularity of various instant messaging apps, remains a crucial means of digital communication. It’s also a common target for cybercriminals, as unencrypted email communications can easily be intercepted and read. Encrypted emails tackle this vulnerability by encoding the messages using advanced algorithms, ensuring only the intended recipient can decrypt and read them.
Using Encrypted Emails on /e/OS
/e/OS comes equipped with a built-in mail app that, by default, is able to use PGP (Pretty Good Privacy) encryption, a widely used encryption and decryption program. Here’s how to set up encrypted emails on your /e/OS device:
- Open the Mail App: Launch the built-in mail app on your /e/OS device.
- Add an Account: If not already done, add your email account.
- Enable Encryption: In your account settings, locate and select the security or encryption settings. Follow the prompts to enable PGP encryption for your emails.
- Generate or Import PGP Keys: The next step is to either import your existing PGP keys or create new ones within the app. Remember, you will need to import both the private and public keys.
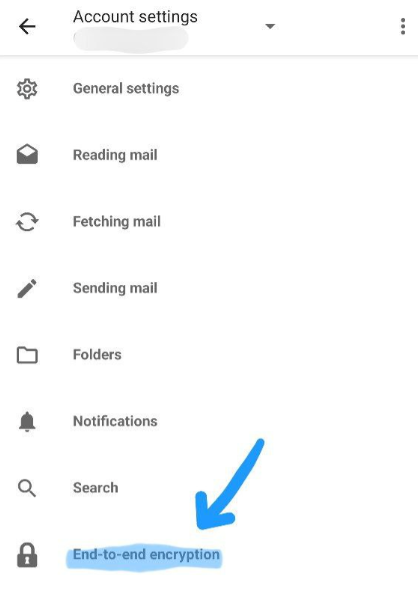
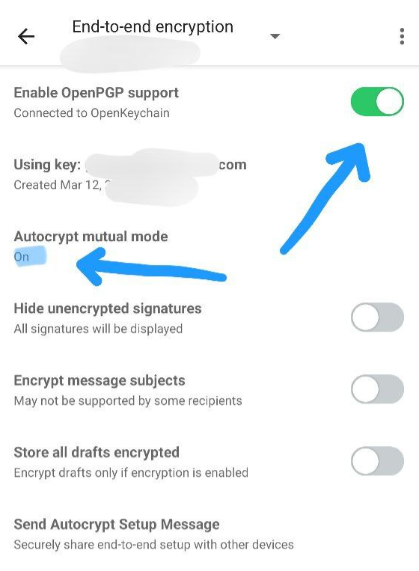
Creating and Importing PGP Keys in /e/OS with OpenKeyChain
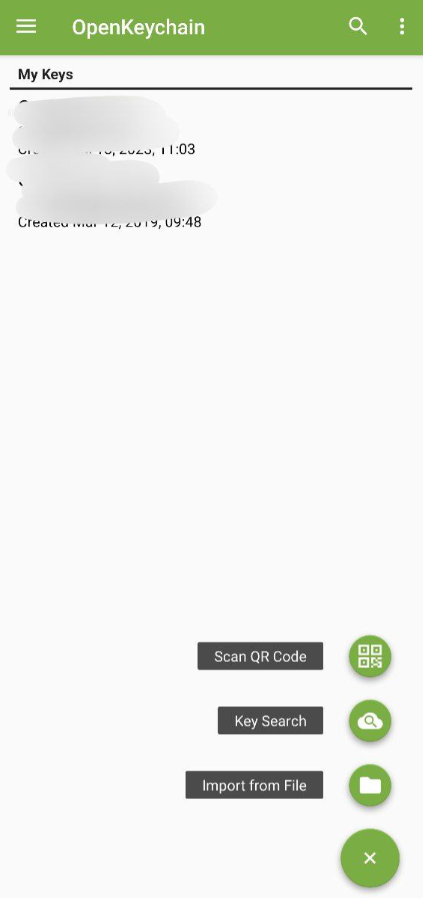
/e/OS employs OpenKeyChain, an open-source application, to manage your encryption keys. Here’s how you can create or import your keys:
- Creating Keys: Open the Mail app and navigate to “Settings.” Select your account, scroll down to “Encryption,” then “Configure PGP.” Tap “Generate” and follow the instructions to create your key pair using OpenKeyChain.
- Importing Keys (if you already have some keys configured for your email address): Open the Mail app, go to “Settings,” choose your account, then find “Encryption.” Click “Configure PGP” and then tap “Import.” Import both your public and private keys with OpenKeyChain.
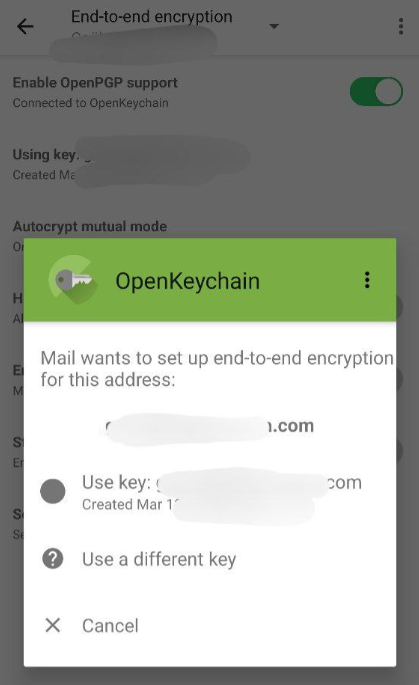
Now your account is set up, you can write emails as you normally would. An option to encrypt the message will present itself before you send the email.
Exporting Keys from Thunderbird:
Thunderbird users can also export their keys for use on /e/OS:
- Open Thunderbird and navigate to “Account Settings.”
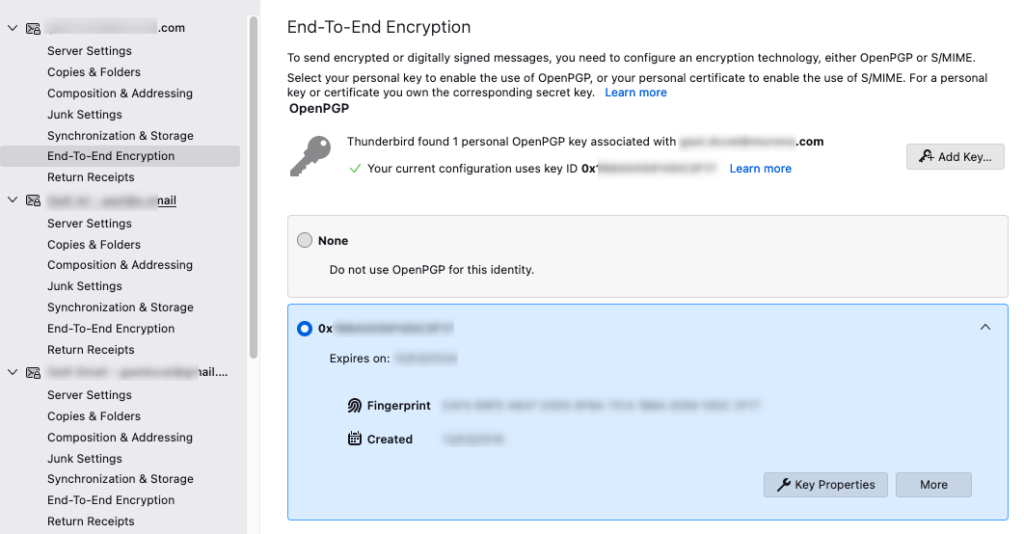
- Select “End-To-End Encryption” then “More” in your key section.
- Choose the key pair you wish to export and click “Export.” Make sure to export both your public and private keys.
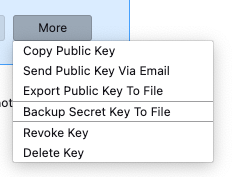
- You will be prompted to set a secret key password, that is used to protect the content of your secret key. You will have to use it to unlock your secret key in /e/OS mail when you want to decrypt encrypted messages.
This is the export process for Thunderbird, but similar private and public keys export are generally available in other email clients such as Outlook.
Transferring Exported Keys files to /e/OS Device
There are several ways to transfer exported keys to your /e/OS device:
- EASIEST: Secure Messaging Apps: You could also use secure messaging apps like Signal, Telegram, Matrix… to send your keys to your device. If using Telegram prefer end to end encrypted message (“Start secret chat”).
- Direct Transfer: If your device is connected to your computer, you can directly transfer the files into a secure folder on your device. This needs to have ADB installed on your computer, and enable it in /e/OS Developer options…
- NOT RECOMMENDED! Email: You could attach your exported keys to an email and send them to an account accessible from your /e/OS device. Don’t do this unless you are sending an encrypted email 😉
Remember to delete the transferred keys files from their original location and any intermediate locations once the import process is complete to maintain your security.
Introducing Autocrypt
Autocrypt is an important addition to email encryption, making the process more user-friendly. It simplifies key management by automatically exchanging and updating encryption keys between communicating email addresses.
When you send an email to a recipient, Autocrypt includes your public key in the email headers. When the recipient replies, their email client automatically extracts and stores your public key. From that point forward, their client can automatically encrypt emails to you. This removes the need for manual key exchange and simplifies the use of encrypted email.
Autocrypt also maintains user flexibility. It allows manual override when necessary, ensuring control remains with the user while offering simplified email encryption.
End-to-End Encryption with Various Online Email Services
Using end-to-end encrypted emails is not limited to specific email services. Many popular email providers support end-to-end encryption, ensuring your emails remain private and secure. Notably, services like Murena.io, ProtonMail, and Tutanota offer robust encryption options that work seamlessly with /e/OS. This wide range of compatibility ensures you can maintain your security and privacy across various platforms, offering greater flexibility and choice.
Understanding Email Encryption: How Your Messages Stay Secure
Email encryption is a method that safeguards the content of an email from being read by entities other than the intended recipient. This is achieved through Public Key Infrastructure (PKI), a system of digital certificates, public-key cryptography, and certificate authorities (CAs). Let’s break it down using our fictional characters, Alice and Bob.
Key Generation and Distribution
Alice and Bob each generate a pair of keys: a public key and a private key, also known as a secret key. The public key, as the name implies, is publicly available and can be freely distributed. The private key, on the other hand, is kept secret and never shared.
Sending an Encrypted Message
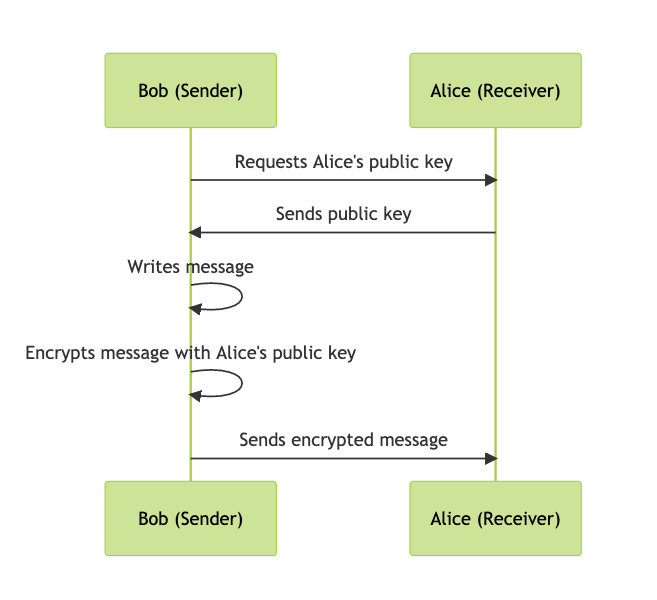
Let’s say Bob wants to send an encrypted email to Alice. Here’s how it works:
- Bob composes his email message.
- Before sending, Bob encrypts his message using Alice’s public key. It’s critical to note here that this encryption can only be done with Alice’s public key, not her private key or even Bob’s own keys.
- The encrypted email can now only be decrypted with Alice’s private key, which she has kept secret. In other words, even if someone intercepts the email during transmission, they won’t be able to read it without Alice’s private key.
Receiving an Encrypted Message
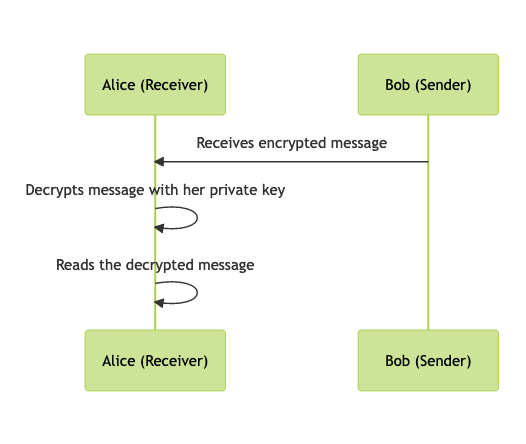
When Alice receives the encrypted email from Bob:
- Alice uses her private key to decrypt the email. The decryption process transforms the encrypted email back into its original, readable form.
- As the only holder of her private key, Alice is the only person who can decrypt the email. This is how the confidentiality of the email is preserved.
The process is reciprocal; if Alice wants to send an encrypted email to Bob, she will use Bob’s public key to encrypt the email, and Bob will use his private key to decrypt it.
Conclusion
Adopting encrypted emails on /e/OS is a crucial step towards improved digital privacy. It may seem daunting at first, but the security benefits greatly outweigh the initial learning curve. In the contemporary digital world, privacy is not just a luxury—it’s a right we all should proactively defend.
AI-augmented Gaël Duval. July 19th 2023.
More about /e/OS: https://e.foundation — More about Murena products & services: https://murena.com
Follow me on @gael_duval on Twitter, @gael@mastodon.social on Mastodon.
